[Project Name]
A privacy-first suite of quantum-secure tools — finally, privacy that doesn't ask permission.
See it in action
Use the demo — right here, right now!
Password Vault
Your credentials are protected with post-quantum encryption — accessible only to you, even when synced across devices.
Encrypted Chat
Send private messages with true end-to-end encryption and zero metadata leaks. Only you and your contact can read them.
Secure by Design
Built from the ground up for privacy, with no third-party trackers, no ads, and no hidden data collection.
Zero-Knowledge Sync
Your data is encrypted before it leaves your device and only decrypted when it returns. We never see your secrets — and never can.
Quantum-Resistant Encryption
Future-proof your privacy with cryptographic algorithms built to withstand even quantum computer attacks.
Modular Privacy Tools
From passwords to chat to secure notes — choose what you need and control how your privacy is protected.
Quantum-Secure Storage
Password Manager
Protect your logins with post-quantum encryption designed for the future. Organize accounts, autofill credentials, and generate strong passwords — all under your control. Zero tracking. Zero compromise.
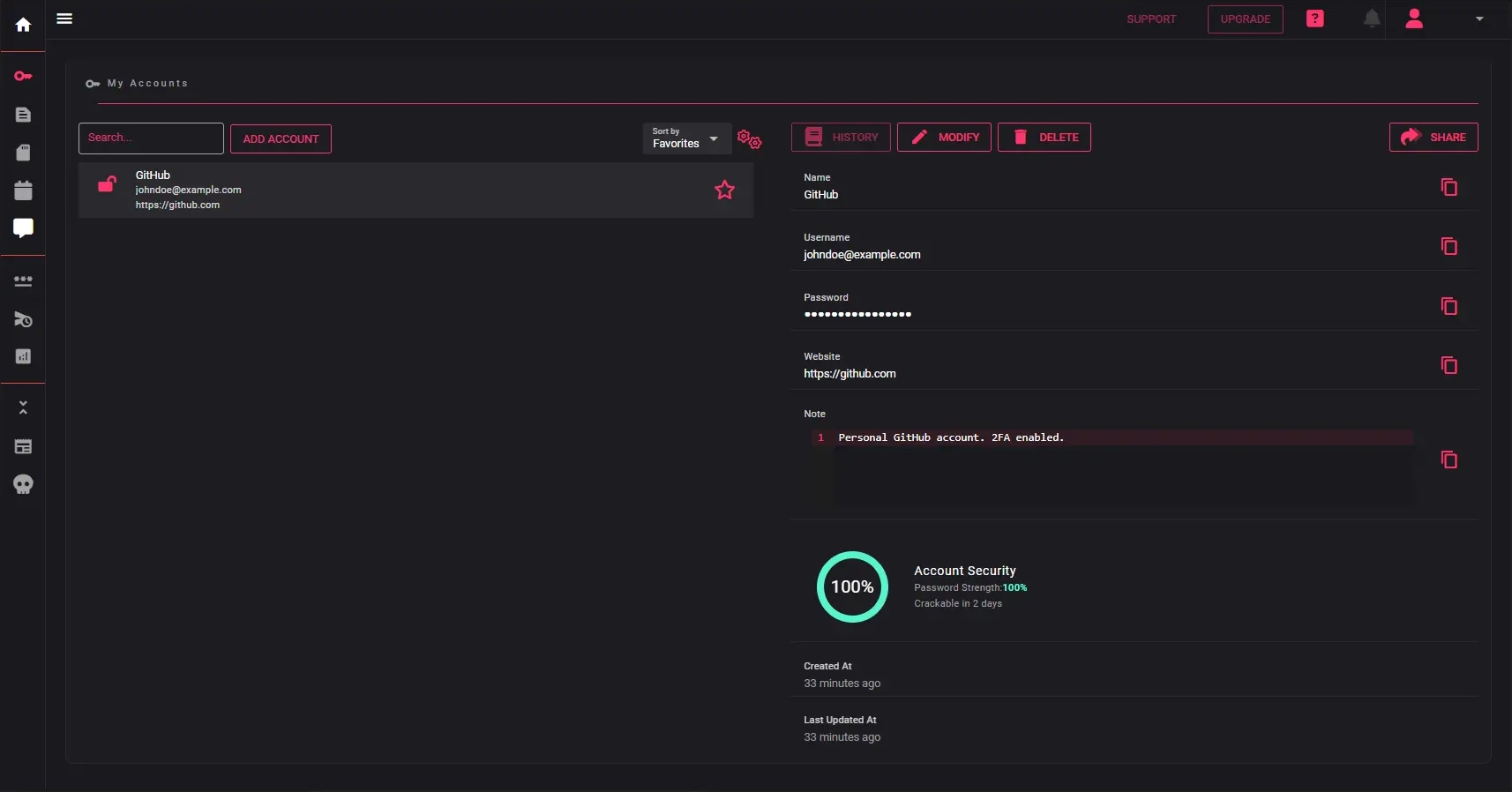
End-to-End Encryption
Private Chat
Communicate freely without ever sacrificing your privacy. Our chat uses quantum-resistant keys and true end-to-end encryption — messages are encrypted before they leave your device and decrypted only on the recipient’s. No backdoors, no eavesdropping, no metadata mining.
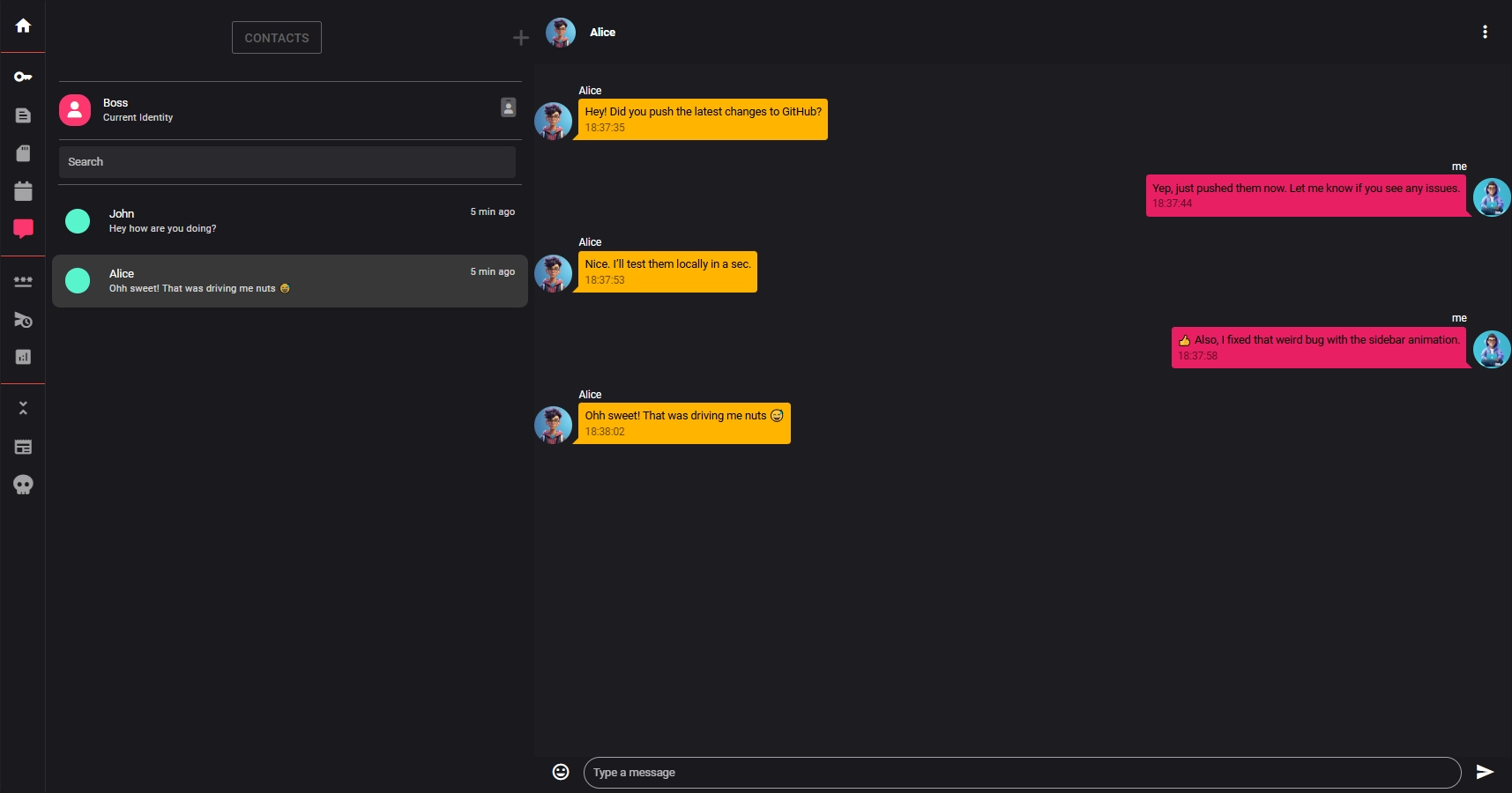
On the Horizon
More Coming Soon
We're just getting started. Encrypted notes, file storage, private calendar, and even more privacy-first tools are on the way — all with zero-trust design and post-quantum security.
Pricing
A license for every need
Pro I - 6 months
$$$ / per month
Limited Time Only
- Purchase 1 Get 2
-
Receive 2 licenses
- Founder Status
-
License prices will never change
- End-to-end encryption
- Quantum-safe key exchange
- Post-quantum message signing
- Zero-knowledge design
- Password Manager
- Quantum-safe Chat
- Security Enhancements
- Planned & Future Features
- And more...
Pro II - 12 months Best Deal
$$$ / per month
Limited Time Only
- Purchase 1 Get 2
-
Receive 2 licenses
- Founder Status
-
License prices will never change
- End-to-end encryption
- Quantum-safe key exchange
- Post-quantum message signing
- Zero-knowledge design
- Password Manager
- Quantum-safe Chat
- Security Enhancements
- Planned & Future Features
- And more...
Pro III - 24 months
$$$ / per month
Limited Time Only
- Purchase 1 Get 2
-
Receive 2 licenses
- Founder Status
-
License prices will never change
- End-to-end encryption
- Quantum-safe key exchange
- Post-quantum message signing
- Zero-knowledge design
- Password Manager
- Quantum-safe Chat
- Security Enhancements
- Planned & Future Features
- And more...
FAQ
Answers to all your questions
While [Project Name] is designed to provide strong privacy and end-to-end encryption, and we take measures to protect against certain attacks like man-in-the-middle (MITM), memory attacks, and more — we cannot protect you from threats such as:
- Shoulder surfing: People watching your screen while you type or read.
- Compromised or bugged devices: Malware, spyware, or keyloggers installed on your device.
- Bad security practices: Sharing your master password will result in privacy breaches.
